If you are in the government consulting or the cybersecurity space, more than likely you’ve been in meetings or office conversations discussing one of the most sophisticated third-party software attacks comprising access to U.S. Government networks. At the conclusion of last year, it was revealed that thousands of top global corporations who were affected by the vulnerability SolarWinds Orion vulnerability—the sad reality however is that even two months after its detection, we do not quite understand the full scope of the attack.
As Federal agencies collaborate and further details emerge, the cumulative collection of evidence, identifying threat actors, and sharing our results with one another will further mature our understanding of this event and also prepare U.S. to sustain ourselves against technically sophisticated adversaries. While there is no easy solution to cyber defense, understanding these attacks can help develop a path forward.
Understanding the SolarWinds Cyber Attack
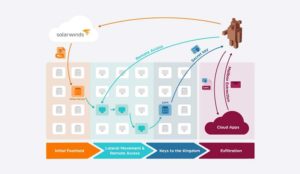
On December 13th, 2020, the perfect plot to a Tom Cruise movie unfolded– Microsoft, FireEye, SolarWinds, and the U.S. Government issued a coordinated report that SolarWinds was victim to a supply chain attack which apparently occurred much earlier in the year yet went undiscovered. Also called a value-chain or third-party attack, this occurs when a threat actor seeks to infiltrate an organization through an outside partner with access to your systems and data. While supply chain attacks are not common, this specific attack was particularly damaging as it involved hackers plugging malware into SolarWinds’ Orion software (which was later distributed to some 18,000 clients).
No alt text provided for this image
Considering this scale of the SolarWinds breach, and the reliance of government on private IT infrastructure management stacks, it is likely that we will witness some amount of regulatory change as a result of Agency collaboration. According to ThreatPost, SolarWinds was the “perfect target” because Orion software had full visibility into an organization’s network. As DoD, DHS, NSA and many more agencies collaborate on the hack, much if their focus will be assessing the damage and depth of the hack, patching up any remaining vulnerabilities, and rooting out hackers who may have used the initial breach to gain “persistent” access to sensitive networks. Rather than downloading all critical data immediately, the attackers used their access to install additional backdoors and cover their tracks, allowing them to monitor developments over the course of the year. In other words, the hack remained ongoing but also undetected for quite some time.
What Needs to Happen
Collection of Evidence
Initially, leading cybersecurity company FireEye disclosed on 12/13/2020 that it was hacked by a threat actor showing all the signs of a nation-state sponsored hacking group, during a breach investigation. The following day, FireEye alerted SolarWinds CEO Kevin Thompson that the Orion product contained a vulnerability in accordance with the cyber-attack.
Shortly after these events, the National Security Council held a meeting at the White House to discuss a breach of multiple government agencies and corporate businesses. That same day, FireEye the disclosed to the public what it had found: a threat of staggering scale and terrifying subtlety.
Note however, how many different players were involved in these conversations? First, FireEye passed its detection to SolarWinds, which then disclosed to its users including the government and its many agencies. The next few months will be dedicated to all of these organizations exchanging notes on the attack and truly understanding its affect through detailed collection of evidence.
Identifying the Victims
The current list of known organizations that were hit by the SolarWinds supply chain attack include: FireEye, U.S. Department of the Treasury, U.S. National telecommunications and Information Administration, U.S. Department of State, The National Institutes of Health, DHS, DOE, NNSA, Microsoft, and Cisco, with more likely to be announced over the coming weeks. AS such, the Cyber Unified Coordination Group (UCG) composed of the FBI, CISA, and ODNI with support from the NSA, have coordinated a joint operation investigating the origins of the SolarWinds data breach. This group will continue to identify the victims of this attack, but given the distribution of the Orion software, this will take time.
Sharing Results and Engaged Collaboration
Victims of the attack have been encouraged by the UCG to share any information pertaining to the SolarWinds attack. Microsoft, which has been headlining the effort in publishing forensic data on the malware, states that the backdoor enabled the threat actor to emulate elevated group policy permissions, enabling access to confidential data. Further forensic details claim that the attackers could compromise internal Microsoft accounts, with one being used to view the source code for their software. Given the long list of now identified and still potential victims of the breach, it is sufficient to say that collaboration between the users of Orion will have to remain strong.
Defense Moving Forward
Proper oversight of third-party cybersecurity risk mitigation strategies will become critical in a post SolarWinds era. Cybersecurity vendors may be asked to do self-assessments, allow customer visits and audits, or purchase cyber insurance. Companies should review how third parties access their confidential data to make sure that correct policy permissions are enforced adequately. Fundamental changes to the United States cybersecurity policy are already underway, as the recently inaugurated executive office vowed to elevate cybersecurity as ‘imperative’ and say they will not stand by idly in the face of cyber attacks impacting the U.S. Government or its people.
Share your thoughts on the SolarWinds Hack in the comments below…
-Narjis Ali,CEO Sure Secure Solutions
—
About Sure Secure Solutions
A leader in providing innovative IT solutions to the federal government and private sector, Sure Secure is a woman-owned small business specializing in cloud services, web development, cybersecurity, and data analytics. Sure Secure is the Managing Venture for the Secure Shiva JV on GSA Stars 2. A services provider to an array of federal clients including NASA, USDA, CBP, FEMA and the U.S. Army, Sure Secure Solutions has been recognized as the Small Business Prime Contractor several times and also received the Outstanding Performance Award by the NASA Chief Engineer. Sure Secure Solutions is also the Small Business Prime Contractor of the Year 2016 for SBA Region 3.

