The impacts of COVID-19 have yet to fully be quantified as we witness a complete paradigm-shift in how businesses conduct day-to-day operations. As many small businesses hastily transition to a work-from-home setting, security and IT respondents are concerned about an increasing number of attack vectors which have been increasingly creating threat vulnerabilities and even incidents. Cybercriminals have adjusted their social engineering tactics, placing a greater emphasis on COVID-19. Proper network hygiene is imperative with the drastic increase in public health related phishing campaigns attempting to impersonate ministries of health or other public services.
It’s an ugly truth to see how this pandemic has not only shaken up the global business landscape, affecting fundamental day-to-day operations, but malicious users have exploited the circumstances to conduct attacks on vulnerable businesses or those unprepared for the abrupt shift in daily operations. The following are the most reoccurring threats experienced since the beginning of state-wide quarantines and mandated telework in mid-March 2020:
Phishing campaigns
Cybercriminals are impersonating authoritative government organizations such as the World Health Organization (WHO), the Centers for Disease Control (CDC), or other ministries of health to distribute malware or obtain fraudulent donations. These criminals are preying off the uncertainty that many consumers and employees have regarding the present pandemical environment.
These emails might ask you to open an attachment to view the latest COVID-19 statistics, with some more advanced algorithms even referring to your geographical area. Should one of these malicious links be clicked, it’s likely that malicious software could be downloaded to your device along with a myriad of other security concerns.
Solutions:
Employee trainings on carefully vetting through unaccustomed emails is critical to protecting against these types of attacks. An example phishing attack utilizing the Centers for Disease Control (CDC) as bait:
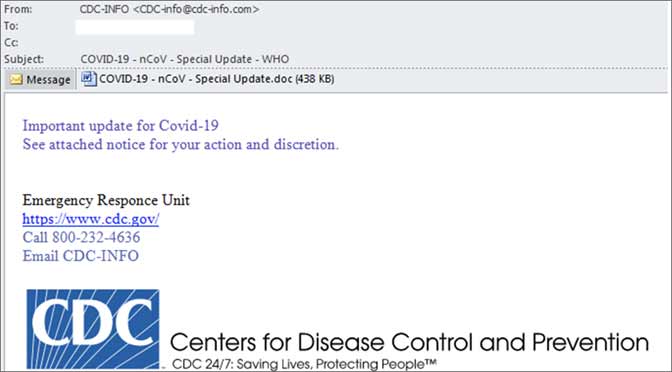
Figure 1: Phishing message targeting U.S. citizens Source: http://www.crowdstrike.com/blog/covid19-and-malspam/
Flagging emails external to the company, proper patching, and utilization of Outlooks’ tools to implement a community-wide blocklist of COVID-19 related emails, are all measures that can be taken to defend against phishing campaigns.
Proper staff education, with the use of practical guides on what to do if their device is compromised, will help reduce potential successful attacks on your network. Reinforcing a no blame culture can also ensure confidence in staff to report incidents, allowing proper entities to deal with, and mitigate the consequences.
Consider archiving offline copies of critical resources that are unattainable by any online administrator privileges.
Credential Stuffing
Credential stuffing, a type of cyberattack in which stolen account credentials (typically consisting of username and/or email address) lists along with their corresponding passwords, (often from a previous data breach) are used to gain unauthorized access through large-scale automated login requests against web applications. Successful credential stuffing can also stem from victims of phishing campaigns, giving cybercriminals further resources to conduct these attacks. Given online collaboration services have exploded in popularity, many companies have turned to resources such as Zoom to host their online meeting space.
Unfortunately, the week of April 13, 2020, Zoom was condemned by several negatively-focused headlines citing 500,000 hacked Zoom accountswere being sold on the Dark Web. Interestingly, Zoom didn’t experience a data breach, and there was no “Dark Web data breach” to be reported of, either. Rather, a majority of these accounts have been traded, sold, or freely given away as part of various credential stuffing lists for several years.
Researchers at a cybersecurity research firm Cyble had successfully found and purchased about 530,000 Zoom accounts via hacker forums on the Dark Web. Cyble stated it was able to purchase these accounts for $0.0020 each, with some accounts being given away to enable “Zoomboming” attacks.
Solutions:
It’s imperative that companies mandate the use of strong, non-reused passwords within their organizations to better protect themselves from potential credential stuffing attacks, as well as maintain their security processes.
Employees should be encouraged to use password managers to regularly manage accounts and follow instructions to reset passwords at regular interims.
Distributed Denial of Service (DDoS) Attacks
Downtime from an attack is even more detrimental with a remote workforce. Larger remote workforces can even act as an unintentional Denial-of-Service DoS attack, simply because more users are attempting to access company services simultaneously. Reports across cybersecurity research firms have outlined that DDoS attacks skyrocketing during the pandemic. Specific statistics outline that in comparison to Q1 2019, DDoS attacks rose by over 278% in Q1 2020.
Solutions:
Understanding that unexpected traffic peaks are more likely to be encountered given that there are more users accessing web-based applications presently.
Conducing fault tolerance analysis of company infrastructure can help identify weak nodes and pinpoint at which point your network may require an increase in stability.
BEC Scams
With email utilization at an all-time high, malicious spoofing of known addresses can lead to financially devastating outcomes. Business Email Compromise (BAC), also known as an Email Account Compromise (EAC) scams, criminals send out messages that appear to originate from known sources making legitimate requests. Several noteworthy examples by the FBI help outline what a typical BEC scam can appear like:
A vendor your company regularly deals with sends an invoice with an updated mailing address.
A company CEO asks her assistant to purchase dozens of gift cards to send out as employee rewards. She asks for the serial numbers so she can email them out right away.
A homebuyer receives a message from his title company with instructions on how to wire his down payment.
According to the FBI’s Internet Crime Report, the bureau received approximately 24,000 complaints concerning BEC fraud last year, with losses totaling $1.7 billion, accounting for nearly half of all cybercrime-related losses in 2019.
While impersonating company executives, attackers are e-mailing lower-level employees requesting urgent, confidential wire transfers to alleviate unexpected issues arising from COVID-19. Malicious software can also infiltrate company networks and gain access to legitimate email threads regarding billing and invoices.
Solutions:
For the duration of the public health crisis and beyond, companies will need to increase vigilance of BEC-related scams. Last minute changes to wire instructions, communication platforms, or the refusal to communicate through voice/video platforms are all signs of potential BEC scams.
The FBI also recommends the use of multifactor authentication for email services, in addition to prohibiting automatic forwarding to external addresses.
Conclusion
Given the drastically altered landscape caused by COVID-19, open communication with work teams and employees about the changes to work life are crucial aspects of protection from attacks. Briefings on company-wide policies for preferred email preferences, the use of multifactor authentication, standard operating procedures for using Remote Desktop Protocol, and known social engineering tactics such as BEC scams are critical to adaptability during this time to maintain security standards.
Sure Secure Solutions is an award-winning, woman-owned small business specializing in cloud services, web development, cybersecurity, and data analytics with prime contracts at NASA, USDA, and the U.S. Army. Sure Secure Solutions is the recipient of the Small Business Prime Contractor of the Year award for the fourth time at NASA.
Narjis Ali, CEO of Sure Secure Solutions is a frequent speaker on entrepreneurship, cyber and cloud security, and non-profit leader. Narjis has worked closely with the SBA Washington Area District Office (WMADO) and is an alum of the SBA Emerging Leaders Program and Goldman Sachs 10K Small Business Program. Narjis can be reached at narjis.ali@suresecuresolutions.com.
Sources:
http://www.businessinsider.com/500000-zoom-accounts-sale-dark-web-2020-4;
http://home.kpmg/xx/en/home/insights/2020/05/rise-of-ransomware-during-covid-19.html;
http://www.crowdstrike.com/blog/covid19-and-malspam/;
http://www.eset.com/int/about/newsroom/press-releases/products/brute-force-attacks-targeting-remote-access-increased-during-the-covid-19-pandemic-eset-confirms/; http://www.csoonline.com/article/3542895/attacks-against-internet-exposed-rdp-servers-surging-during-covid-19-pandemic.html;
http://www.cpomagazine.com/cyber-security/report-says-ddos-attacks-increased-by-over-500-because-of-the-covid-19-pandemic/;
http://www.fbi.gov/scams-and-safety/common-scams-and-crimes/business-email-compromise; http://pdf.ic3.gov/2019_IC3Report.pdf; http://www.jdsupra.com/legalnews/fbi-warns-companies-to-be-vigilant-as-53073;
http://www.bankinfosecurity.com/rdp-brute-force-attacks-rise-during-covid-19-crisis-report-a-14206